Published 2017-01-15.
Last modified 2025-03-30.
Time to read: 4 minutes.
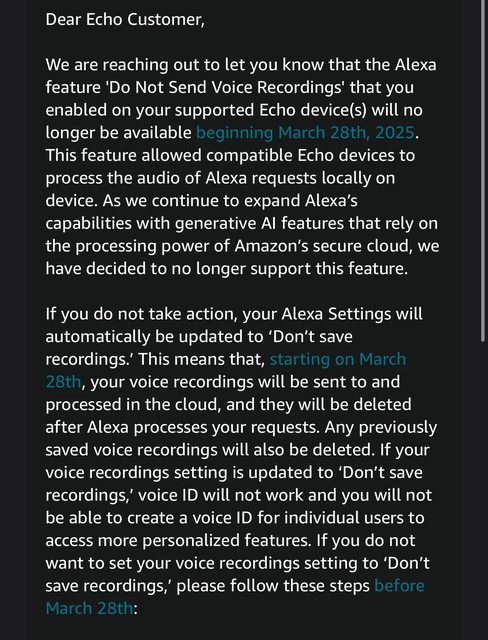
2025-03-28 Privacy Change
Amazon is ending the option to not send Echo voice recordings to the cloud
2022-04-27 Update
Amazon is monetizing your conversations, according to a study published by 10 researchers at the University of Washington, the University of California-Davis, the University of California-Irvine, and Northeastern University. The study is titled “Your Echos are Heard: Tracking, Profiling, and Ad Targeting in the Amazon Smart Speaker Ecosystem”.
Abstract
Smart speakers collect voice input that can be used to infer sensitive information about users. Given a number of egregious privacy breaches, there is a clear unmet need for greater transparency and control over data collection, sharing, and use by smart speaker platforms as well as third party skills supported on them. To bridge the gap, we build an auditing framework that leverages online advertising to measure data collection, its usage, and its sharing by the smart speaker platforms.
We evaluate our framework on the Amazon smart speaker ecosystem. Our results show that Amazon and third parties (including advertising and tracking services) collect smart speaker interaction data; where Amazon shares it with as many as 41 advertising partners. We find that Amazon processes voice data to infer user interests and uses it to serve targeted ads on-platform (Echo devices) as well as off-platform (web). Smart speaker interaction leads to as much as 30x higher ad bids from advertisers. Finally, we find that Amazon’s and skills’ (apps’) operational practices are often inconsistent with their privacy policies.
Some of the references cited by the paper are disturbing. This is the reference that concerned me the most:
- Alexa has been eavesdropping on you this whole time.
– Washington Post, 2019-05-06.
The short answer: probably not.
A longer answer: Depends on what you mean by ‘listening’. If you mean “is Alexa storing or sending every sound or voice utterance to a server”, the answer is again “probably not”.
A more complete answer: unless all the source code for a device is made available for scrutiny, and the build process is similarly examined, the only way to be sure that device does not have operating modes that are contrary to expectations would be to connect the device to a network monitor that only allows communication with specific servers at designated times. Normal computer security concerns also pose risks; for example, viruses and other malware could be injected into a device could cause it to behave differently.
At Least Echo’s Mute Button Works
Update 2021-01-12 – Amazon Echo’s mute button was reverse engineered.
The mute button appears to be very real and functional. When the button glows red the power is removed from the microphones.
Some Paranoia is Healthy

Mattel’s Aristotle is targeted at children. It uses Microsoft Bing for searching, Microsoft Cortana for voice processing and streams video to the cloud. It can read bedtime stories and play soothing sounds if your child wakes up at the night. It can recognize your children’s imperfect speech, and apparently adapts as they get older and become curious about the world. Aristotle is an AI to help raise your child. Did they do a terrific job or a terrible job? It depends on the factors you take into consideration.
Aristotle can respond to adults differently than to children. Its logging capability is profound. It tracks things like wet diapers and feedings, and can order supplies when asked by an adult.
Aristotle can use object recognition to identify flashcards, or co-opt a toy without electronics and thereby enhance it with sound effects or even another personality.
Mattel has about 500 partners, and they have been invited to build connected toys and apps. The hardware uses 256-bit encryption for all transmissions to Aristotle’s servers, and data is handled internally in compliance with COPAA and HIPAA.
It is not difficult to write code that detects when a child is alone
How hard would it be to write code that detects when the child is alone? If a malicious entity wanted to, they could embed their program in the device, use IP geolocation and other characteristics to identify specific families, and cause the device to behave differently and/or tell the child things when no adults were paying attention. Who knows what malicious software might do?
Open Source To The Rescue

Closed source systems cannot be adequately vetted for public usage. It is conceivable that selected children might become secretly radicalized by their toy. In 1913 Justice Louis Brandeis said “Sunlight is the best disinfectant”. Open-source applications, with updates that can be vetted by any interested party, are the only way to ensure these devices are truly safe.